Platform Development for US Teams (Multi-User, Role-Based, Integration-Ready)
Build a platform your team can operate: roles, workflows, permissions, audit trails, and integrations, not just a bigger app.
Berlin-based senior engineering team, US-friendly collaboration hours, and full ownership by default.
Built for products that must be operated daily by support, ops, and compliance teams.

Role and permission model (RBAC/ABAC) with auth flows
Workflow states/transitions, approvals, and admin console boundaries
Audit logs, observability baseline, and release rollback strategy
Security baseline, data model, migration and API versioning policy
Roles and access grow chaotically, creating security and support incidents
Workflow changes break production without state and migration discipline
Integrations fail silently without retries, DLQ, and monitoring ownership
No admin tooling or audit trail forces manual emergency fixes in production
Role-based core
RBAC/ABAC and auditability from day one.
Workflow-safe
State transitions and approvals stay predictable.
Integration-ready
Events, sync jobs, and adapter boundaries included.
Operable daily
Admin tooling, logs, runbooks, and ownership.
This is for you if
Identity, roles, and workflow control
Platform foundations for multiple user types and operational states.
- •Permission model (RBAC/ABAC) and role boundaries
- •Workflow engine basics: states, transitions, approvals
- •Admin console and moderation tooling
- •Audit log and traceability by entity/action

Integration and operability layer
Reliable connections to external systems without brittle coupling.
- •Webhook/event ingestion and sync job orchestration
- •Retries, idempotency, and dead-letter queue policy
- •Observability: logs, metrics, traces, and alert routing
- •Runbooks and ownership paths for incident response

Data model and release safety
Architecture boundaries that allow long-term platform evolution.
- •Domain map, module boundaries, and API versioning rules
- •Migration strategy and rollback playbook
- •Environment strategy (dev/staging/prod) with CI/CD
- •Security baseline: least privilege and secrets handling
Role rules drift and access bugs multiply,
workflow updates break production behavior,
integrations fail silently without retries and DLQ visibility,
support runs manual SQL due to missing admin controls,
no audit trail means incidents cannot be investigated,
each release becomes stressful because operability was never designed.
We design role boundaries, state transitions, integration safety rails, and runbooks so the platform remains operable.
Get a platform risk review
Platform-specific results from role and workflow-heavy systems
Support and ops can run the system without engineering bottlenecks.
Admin tooling, audit trails, and moderation paths are available from early releases.
Process changes ship without destabilizing existing flows.
State transitions, module boundaries, and migration rules prevent regression chaos.
External dependencies fail safely instead of silently.
Retries, idempotency, and monitoring prevent cascading operational incidents.
Every critical action is traceable for support and compliance.
Action history and traceability reduce incident resolution time and ambiguity.
Platform-first architecture
Domain boundaries, workflow states, and role models defined before scale pain appears.
Operability by default
Admin surfaces, audit logs, monitoring, and runbooks ship with core features.
Integration-safe evolution
Versioned contracts, adapters, and reliability guards reduce breakage from external changes.
Documentation that scales teams
Architecture diagrams, decision logs, and migration playbooks support hiring and handover.
Full ownership
Code, infra, data model decisions, and operational artifacts stay with your team.
From architecture blueprint to operable platform lifecycle

1
Platform blueprint
Artifacts: permission matrix, domain map, workflow diagrams, integration map, and data model draft.

2
Operate-first build
Artifacts: admin console MVP, audit log, queue/retry controls, observability dashboards, and release gates.

3
Scale and evolve safely
Artifacts: module boundaries, API versioning rules, migration playbook, runbooks, and change cadence.
Proof from platform systems
SaaS platform with dynamic page operations
Web Page Generator Platform
Built a role-aware platform with content workflows and scalable generation logic.
What changed: faster controlled publishing with stable admin operations.
See case study
Platform and payment-linked workflows
EventStripe
Delivered platform behavior around event lifecycle and payment-linked operations.
What changed: cleaner operational control and fewer manual reconciliation loops.
See case study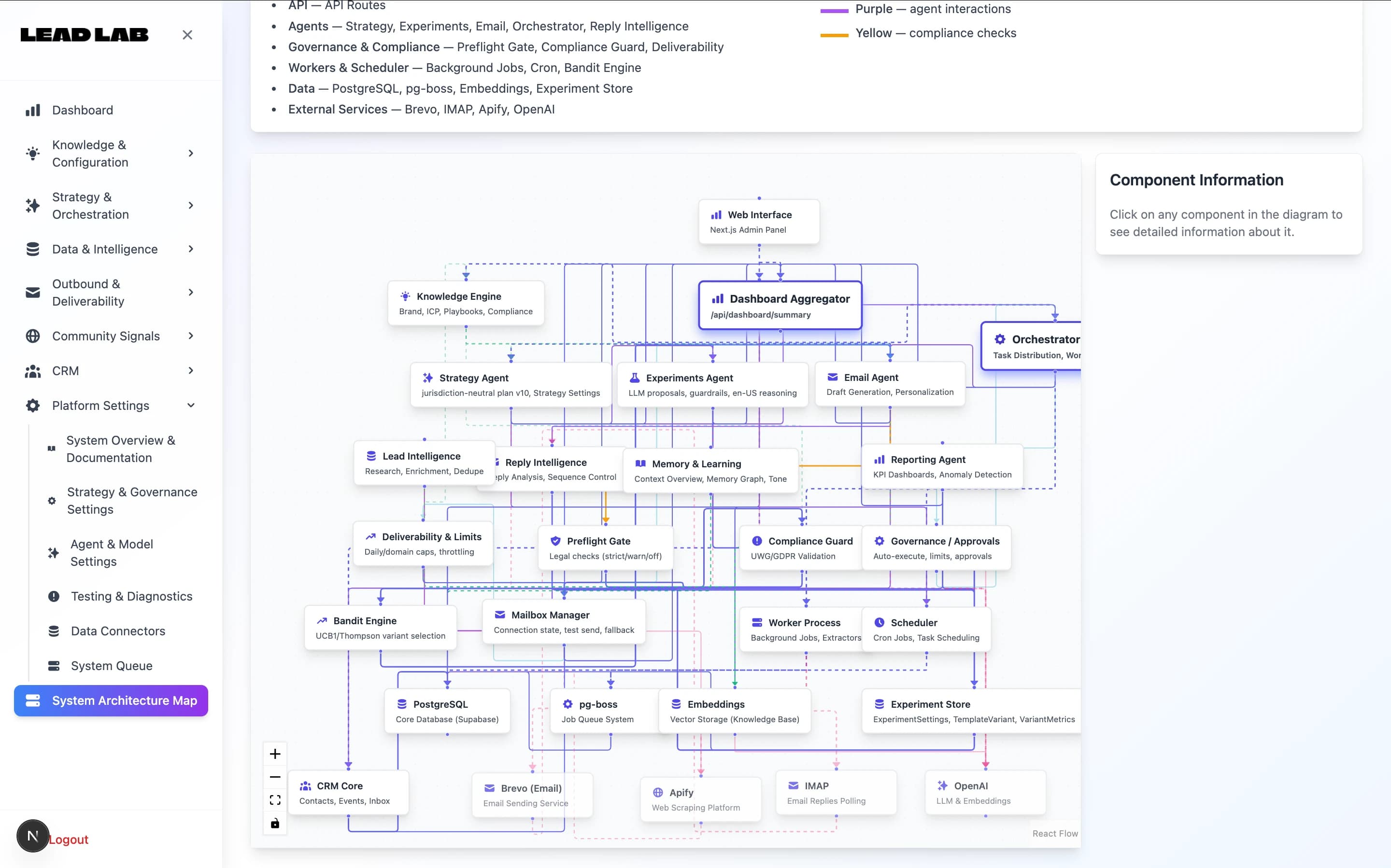
Growth platform data and ops loops
Lead Lab
Implemented workflow-centric data platform components for ongoing product operations.
What changed: improved visibility and faster change cycles for operators.
See case study
High-load operational backbone
VTB Enterprise Reliability Layer
Applied enterprise-grade reliability and observability patterns for critical operations.
What changed: predictable behavior and safer platform evolution under load.
See case studyFrequently Asked Questions
We map actor types and sensitive actions first, then apply RBAC/ABAC boundaries and test role scenarios before release. Access logic is versioned and reviewed as workflows evolve.
Yes. Operability is part of the core scope: admin actions, moderation controls, audit views, and incident-friendly diagnostics are included early.
We choose based on isolation requirements, expected tenant count, performance profile, and operational complexity. The tradeoff is documented before implementation.
Integration safety includes retry policy, idempotency keys, dead-letter handling, and alert routing. Failures are visible and actionable instead of silent.
Choose your track
Pick the path by job-to-be-done so platform scope does not overlap with MVP, web app, or automation work.
